Search the Community
Showing results for tags 'Crypto'.
-
I wrote an article for steemit on why I think the blockchain will end the world as we know it. I would greatly appreciate any feedback that you guys have to give. Here's a link to part 1 and part 2, I didn't realize they had a character limit so I had to make the conclusion it's own post.
- 3 replies
-
- crypto
- blockchain
-
(and 2 more)
Tagged with:
-
Bitcoin: Getting Started What is Bitcoin? Bitcoin is a decentralized digital cryptocurrency. Please review this video: http://www.youtube.com/watch?v=Um63OQz3bjo For anyone looking for a more advanced overview, here is the Khan Academy Bitcoin Course Playlist: https://www.khanacademy.org/economics-finance-domain/core-finance/money-and-banking/bitcoin/v/bitcoin-what-is-it Bitcoin Terms: Address (Public Address): These are the parts of the Blockchain which denote where the bitcoins are. Anyone can generate an address and begin receiving bitcoins. The address can be made public in order to receive bitcoins. Bitcoin, BTC: The Cryptographic bits of data that can be exchanged as a payment system. Bitcoins are divisible a theoretical infinite number of times. There are several names for these divisions including BitCents (BTC x 10-2), mBTC (BTC x 10-3), uBTC (BTC x 10-6) and Satoshi (BTC x 10-9). Block Chain: This is the P2P transaction ledger for Bitcoin. All transactions are stored on the ledger and on every computer connected to the bitcoin network. Older transactions are compressed for efficiency, however it still can take some time to update when a computer has been off for a while. Confirmation: It is possible that bitcoins could be sent fraudulently (through double spends, etc). However, the system is constantly being audited by miners. If a transaction is successful, then it will start acquiring confirmations. It is considered to be guaranteed correct if it has acquired 6 confirmations. You may decide how many confirmations you wish to wait for. Increasing your fee will prioritize the transaction to the miners and will make transactions get confirmed faster. If you do not care how long the transaction takes, you can send the transaction fee free. A significant fee to make the transaction occur quickly is still very small. Difficulty: Bitcions are mathematically released and the difficulty it is to get bitcions is constantly adjusted in order to regulate the release of coins. If coins are being released too fast (more people start mining as BTC price rises) then the difficulty will increase making mining less profitable. Double Spend: A user will try to send bitcoins to 2 addresses simultaneously. The software thinks it has enough coin for both transactions when in reality it does not. Thus, the user is attempting to multiply his purchasing power. This is why miners are auditing the system in order to prevent such fraud. Hash Rate: The rate at which a miner’s (or the bitcoin network) calculates problems for auditing and verifying the blockchain. At the time of writing this, the bitcion network’s hash rate is 4,000,000 Gh/s which means that it performs 4 million billion calculations a second. Key (Private Key): This is what allows you to send the bitcoins in an address. If you lose your private key, you can look at bitcoins in a wallet but you will not be able to send them. Public Addresses can be generated from Private Keys, but Private Keys cannot be figured out from Public Addresses. Mining/Miners: Miners use mining equipment to audit the bitcoin system. They are rewarded with bitcoins as they are being released into the network on a regular, planned basis. Once all bitcoins are released, mining will still continue but will survive on the transaction fees. Mixing: There may be a time where you wish to send coins in a way that is anonymous. A mixing service will allow you to send coins into a pool where your coins get sent somewhere unrelated to the recipient of the coins. The recipient will then get coins from someone else who sent them to the pool. Current fees are around 1% P2P: Peer-to-peer system where there is no central location where the data is stored. It is on everyone’s computer and is shared between users. This means there is no central system you have to go through and shutting down one node will change nothing about the system as a whole. Signature: If one wishes to make known that an address belongs to them, they can transmit a digital signature to the network. This will cause you to lose anonymity. Taint: If coins are sent from one address to another, the system “remembers” where the coins have been. This is called taint. Tainted coins can be mixed and sent to a new address if desired. Taint can potentially lead to linking addresses, but because of mixing it makes it impossible to trace. Wallet: This is the collection of addresses that you own is said to be stored in a wallet. If you use the standard software, the file that stores your addresses is wallet.dat. Can Bitcion be Hacked? The Bitcoin Math itself cannot be hacked unless you took the power of the sun and converted it into computing power for a couple million years. This is theoretically possible, but practically impossible. HOWEVER… The weakness in bitcoin is not the math. There are a few ways in which bitcoin has vulnerabilities. The 51% attack: If there was a situation in which someone can get enough computing power in order to overcome the entire bitcoin system (own 51% of it) then their miners could approve the transactions they want to the detriment of actual valid transactions. The longer bitcoin goes on and the more popular it gets, the more impossible it is for this to happen. Currently, it would take a few super computers to overcome the system and is quickly becoming nearly impossible. YOUR SECURITY!!! The main thing you want to be concerned about is YOUR security. The weakness in bitcoin is not the math of bitcoin, but you not having good protection of your private keys. If you store your private keys in a wallet.dat file on your computer, then I will not try to hack bitcoin. I will hack your computer and copy that file. Thus, precautions must be taken. How Can I Get an Address/Wallet? Computer Client (Think Checking Account) There are several ways to get an address/wallet. If you are just going to dip into the bitcoin network and want an easy way to send small amounts of coin, then the best method is to use one of the many programs available for bitcoin wallets. http://bitcoin.org/en/choose-your-wallet The Bitcoin-Qt is the backbone of the network and the main base client if you want to start. Armory Client is a feature-rich client that I currently use. It allows paper back-ups and many other things. Encrypting a Wallet: If you want to add one step up to your protection, both of those clients allow you to encrypt your wallet by using a passphrase. Make sure the passphrase is complicated. An easy passphrase just creates a vulnerability. You can get a good enough encryption in order to make it pretty secure to store some coins. Backing Up a Wallet: You can copy a wallet.dat file onto a thumb drive, cd, or even write your private key on a piece of paper. In case of a hard drive failure, you do not want to lose your coins. Cold Wallets (Think Savings Account): In order to take away the vulnerabilities to your computer, then you can print out an only paper wallet. You can use the public address to send coins into the wallet and only import the private key at some point in the future when you wish to spend those coins. Some especially paranoid (or they just have a loooot of bitcoins) people will buy a computer that has never touched the internet in order to generate the address and then destroy the computer. For a full description as to how to generate a good paper wallet, read this link: https://en.bitcoin.it/wiki/Paper_wallet If you want to generate some paper wallets, you can go here (be sure to move your mouse around as it helps make the address generation more random): https://www.bitaddress.org/ There are many other cold storage options (and you can come up with your own) but here are some examples that are out there. https://www.casascius.com/ http://www.wired.com/wiredenterprise/2013/03/bitcoin-ring/ https://bitcointalk.org/index.php?topic=156534.0 Many more are probably in use that people do not wish to share. How Do I Get Bitcoins? Exchanges There are many exchanges available. If you wish to look at the list: https://en.bitcoin.it/wiki/Trade#Currency_exchanges Coinbase has been used and is trusted by a few FDR users. *Update: Since making this thread, I have created an account at Coinbase and would highly recommend them for purchasing bitcoins. *Update #2: MMD also has used Coinbase and set up an FDR affiliate link. By using this link to create an account and purchasing at least $100 worth of bitcoin, Coinbase will give FDR $5 worth of bitcoin. A great way for you to get bitcoin and indirectly send a little tip for some of the work Stef and Mike have been doing around bitcoin lately. This link is now the FDR affiliate link: https://coinbase.com/ One of the easiest ways to get bitcoins is to use LocalBitcoins.com (https://localbitcoins.com/). LocalBitcoins allows you to meet up with people (at a public place to prevent theft) and trade BTC for money. Make sure to wait for confirmations before leaving a local bitcoin exchange unless you trust the other person [high rating] (and make sure you give a transaction fee to the network so that this happens in a reasonable amount of time.) If you have any worries at all in a local exchange, do not buy and just check the next person on the list. Bad feelings can easily let you just abort the exchange at any time. Besides exchanging money, there are other options. Faucet Sites: These sites pay you to look at ads or watch videos. I run them sometimes in the background when I’m going to be on the internet all day anyway. You will not make a lot of money on this (a couple cents an hour maybe?) However, if you are just looking for a small amount to tip people with or just a free way to dip in, then faucet sites may be for you. I have used bitvisitor.com in the past. Donations/Tipping: Create an address and put it in your signature in forums or on your website. When you produce content people enjoy, they may send you a tip. Payment: Accept payment for goods or services in bitcoin. Especially if you think prices will go up (or bitcoin just has fewer fees) you can provide discounts for customers who pay in bitcoin. Mining: I would HIGHLY recommend against this until you have spent a lot of time on bitcointalk.org and know what you are doing with mining. Mining can lose you money if you get the wrong equipment. However, some people (especially where power is free or very cheap) are able to make money mining for bitcoins. Of course there are probably many other ways to earn BTC, but these are the basics. Can I Accept Bitcoins Without Having to Hold the Bitcions? Bitpay (https://bitpay.com/) and other bitcoin payment providers allow people to accept bitcoins and get a check for the value of bitcoins at the end of the day. This allows people to accept bitcoins as payment, but not worry about potential fluctuations in price in the bitcoin market. How Can I Send Bitcoins? If you have the coins on a cold wallet, import them into a client. Select “send bitcoins” or the equivalent. Make sure the transaction fee is set where you want it to be. Paste/Type the public address of where you would like them sent. Paste/Type the amount. DOUBLE CHECK THE AMOUNT AND ADDRESS!!! There are no chargebacks with bitcoin and someone may keep excess coins that are sent if they choose to. If you send to the wrong address, then it is most likely that that person will keep them (or they will never be seen again if you somehow really messed up). There are checks in the system to correct toward real addresses; however, double checking should always be performed. Send the coins. What Can I Buy with Bitcoins? A list has somewhat been compiled here: https://en.bitcoin.it/wiki/Trade However, there are probably many, many more who are not on that list and accept bitcoin. An open-source map of bitcoin-friendly businesses has been started here: http://coinmap.org/ Even if you do not end up getting bitcoin, but enjoy the idea it would be awesome if you supported bitcoin-friendly buinesses in your area with fiat dollars as well as with bitcoin if you wish. Where Can I Learn More? http://www.weusecoins.com/en/ https://en.bitcoin.it/wiki/Main_Page https://bitcointalk.org/ http://bitcoin.org/en/ http://www.reddit.com/r/Bitcoin/ http://bitcoincharts.com/ http://blockchain.info/ And many more... At this point I will take a break and ask for feedback. I probably made mistakes, so I would be happy to hear corrections. Do you have a question I didn’t answer? I will answer it below and if I think enough people will have the same question, I will edit this post so that others do not have that question at the end. If you want more information on a topic, I may have some sources or can create another post about it. Thanks for reading!
-
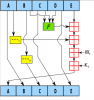
Introduction: I'm in the process of teaching myself how our modern computer cryptographic functions work, and also (eventually) making my own. I started looking into cryptography last July, and have been working on it on and off since then. This thread will consist of my attempts at both recreating the current standards visually in Excel, and developing my own methods. Doing this more as a proof of concept because I am not a computer programmer by trade and such do not know how to make a truly applicable algorithm. If at some point I get extremely daring, I'll try to bring it out of excel and into an actual application. Feedback and input is always welcomed. I can also get into the finer details of the actual Excel formula-side if requested. If unspecified I will simply give the executive summary at every relevant checkpoint. To start the thread it will be a bit of a catch up and a learning curve, but in the followup posts I will try to more fully explain the process/terms. Apologies if I made some mistakes in the very brief description of the algorithms and my recreations. These were completed over six months ago and I'm a little fuzzy on much of the underlying specifics that were being dealt with at the time. Again, as a disclaimer I am not well-versed in computer programming, especially at the bit by bit level, let alone the upper-level language-level. Everything expressed here is to the best of my understanding at the time of posting. As such, if I make a mistake in defining terminology, a concept, etc please correct me otherwise I'm just throwing stuff at a wall and hoping it sticks. Thank you, Songbirdo Recreation in Excel: The recreation starts with the white paper taken from the NIST.gov website: http://csrc.nist.gov/groups/ST/toolkit/examples.html The white papers provide the pseudo-code as well as the function outputs so I may check my work for accuracy. After deciphering the pseudo-code (and looking up a lot of terms on Wikipedia that I don't understand), I attempt to recreate it in Excel. This process has its difficulties as Excel cannot be iterative (a cell cannot reference and write to itself) so additional cells and lines are required for the multiple cycles that these algorithms use. Excel is also very picky with what a 1 (as a number) and 1 (as a piece of text) is. The workaround is simply to use an If/then function to specify the text as a number, and vice versa where needed. Excel also does not have an XOR function (at least my version), and nesting the necessary AND OR functions proved fruitless. So I did a tabular addition and manually carrying the remainders to do the MOD32 additions. For the bit-wise XOR function I just did a simple if/then scenario (where if one is 1 and the other is 1, it will output 0, etc). I tried to colorize by word (the primary color) and then the different shades of that color to help distinguish between each hexadecimal (four bit) sections. (Necessary to keep track of later during the Rubik's twists, see below). The colorization also helped keep track of where each string of the bits were originating from (especially for bit rotations, see SHA-512 spreadsheet and the Wt formulation table - teal blue with speckles of orange red and yellow). SHA-1 (Secure Hash Algorithm): I started with the asymmetric compression function: SHA-1 http://en.wikipedia.org/wiki/SHA-1 It is basically a password encryption function. One-way, "cannot" be reversed. Pictorially it looks something like this: ABCDE are five separate "words" of 32 bits (1's and 0's) each in length. The <<<< are bit rotations, F is a function, the box with a cross through it are XOR (exclusive or) boolean algebra, Wt and Kt are words based on your password (input). After working out the translational problems with Excel I got a working model of the SHA-1 Preview: Link to the full spreadsheet:https://mega.co.nz/#!44U1lZAT!VdAt8f8F9f9Zxd7a8jqkPYDgelwNLD3Cx543II_K2bs Compare the hash values you obtain in the spreadsheet with: http://www.fileformat.info/tool/hash.htm?text=abc SHA-2 (Secure Hash Algorithm): The SHA-1 is no longer as widely used as it once was mainly because it isn't as secure as it used to be. So I moved onto the SHA-2 (specifically the SHA-512 for 512 bit encryption). http://en.wikipedia.org/wiki/SHA-2 The underlying algorithm looks pictorially like this: Muuuuch more complex. This is a 512 bit (8 - 32 bit words). Thankfully the white paper had step-by-step outputs so I could check my work. I made three or four minor mistakes that completely changed the outcome. Picture of one cycle comparison (each color is a different Word, Blue = A, Red = B, etc) Link to the full spreadsheet: https://mega.co.nz/#!09UBkR6D!WXl1-wohIAvaEl0RZD_vISlxgJ1NSKXr50K09U90eHQ AES (Advanced Encryption Standard): Onto what I'm working on now! The AES Block Cipher is fancy way of saying "encrypting information (think file encryption) that can be reversed with the password". http://en.wikipedia.org/wiki/Advanced_Encryption_Standard The AES appears to use a combination of 128 (10 cycles), 192 (12 cycles) and 256 (14 cycles) bit encryption and applying four functions per cycle. It encrypts based on an array of bits (2D representation of the bits) instead of a string (one dimensional representation of the bits) like the SHA-512 did. The fact this uses an array excites me as this means its proof that these encryption algorithms can be brought to three dimensions (and more!). And then all sorts of cool functions can be applied, I'll give you a hint: Anyway, need a working AES model before getting into the Rubik's rotations, but I've already got separate spreadsheets to assign and rotate bits in a similar fashion (or at least similar block sizes, may need to adjust them to the correct bit size of the block ciphers) The four functions of the AES are SubBytes (Byte substitution), ShiftRows (similar to a bit rotation, except for the whole row of bits), MixColumns (which I'm currently figuring out) and something called a Round Key value (unsure what this is for as of now, but I know it's based on your key/password). Screenshot of Current Progress (4/1/2014): SubBytes (COMPLETED): take a cell, and based on what the 8 bits are, substitute it with a different 8 bits (shown in hexadecimal format): Copied from the white paper. The colorization was done to error check my typing. I did make an error, enclosed in a box. The lower right one was 93, where it should have been 9e. The columns on the right are reformatting the original table so that the VLOOKUP excel function can be utilized. ShiftRows (COMPLETED): MixColumns (RESEARCHING): RoundKey (RESEARCHING): Reversible XOR (Exclusive Or): One of the really cool things I realized about the XOR function is that it's reversible by reapplying the imput. Which is why the Block Cipher works symmetrically to encrypt and decipher your files. That's the fundamental difference between this block cipher and the compression function SHA. For example, say your (key) is "1" If you (file) is 1 or 0 1 (key) XOR 1 (file) = 0 (output) 1 (key) XOR 0 (file) = 1 (output) So your encyrpted (file) is either 0 if your starting was 1, and 1 if your starting was 0. Apply the key again: 1 (key) XOR 0 (output) = 1 (file) 1 (key) XOR 1 (output) = 0 (file) Tada! Back where you started. The SHA uses a Mod 32 summation to combine separate words. Think of Mod summation like a 12 hour face-clock. It goes from 1 to 12, then goes back to 1, and keeps going around. Mod 32 is like a clock except for 32 bits (the number itself is actually 232 where a clock is just 12). This means when you reach 232, it ticks over and starts from 0 again. If you try to undo that, you don't know if it cycled once, twice, or even at all. This is part of the reason why the compression functions are nearly impossible to crack. This large summation happens 80 times in the SHA-512, consisting of about 10 rows of bits: The largest remainder I've seen (how many times the specific bit cycled between 1 and 0) is nine. So the 232 "clock" looped around up to nine times per cycle, at two positions in the algorithm,and again over 80 cycles, or a total possibility of looping up to 1440 times! Customizable Encryption Algorithms: I had the realization one day driving home that you need two things in order to break an encryption (excluding the obvious: computer, electricity, network, etc etc...). You need the key (password) AAAND you need the algorithm in which it was encrypted. Without both, you cannot possibly hope to decipher the encrypted file. Where the Rubik's Cube "twist" comes into play (once the AES is brought to the third dimension) is the ability to scramble a block or multiple blocks beyond recognition. The rotation algorithm in which you scramble it would be user-chosen and so the encryption algorithm itself becomes customizable. Even if you manage to steal a key (password) to access the files, without the Rubik's rotation algorithm as input, you don't have the appropriate algorithm to decipher it. It's like finding a key on the side of the road but not knowing which lock it was intended to open. Imagine a company having a personalized encryption algorithm proprietary to that company and their network. Talk about secure information storage! This reminds me of what the banks and other online companies use for authentication: two really big prime numbers multiplied together. They store the product openly, but without the two prime numbers to generate the product you cannot be authenticated.
- 4 replies
-
- Cryptography
- crypto
-
(and 8 more)
Tagged with:
-
RE: Bit Message Site URL: https://bitmessage.org/wiki/Main_Page One of my bit message identities: BM-NB3CWfYYHNdv624xb7qXQskX3hkrBbD2 You can write to me anonymously and I guess with privacy to the above address. You can also add addresses to subscribe to. For example Cryptojunky's address: BM-2DBXxtaBSV37DsHjN978mRiMbX5rdKNvJ6 I subscribed to it and this week got the following messages/broadcasts. Anyways, thought I'd share this with the group, I'm always interested in privacy and decentralized tools to do it and to keep people connected. ~docgnu~ Greetings fellow Cryptojunkies! I just put together and published a post on using PGP/GPG to encrypt traditional email. In light of continuing revelations that many email service providers may have compromised security, I felt it appropriate to cover the topic. The article can be found at the below link: http://cryptojunky.com/blog/2013/11/01/encrypt-all-the-things-with-pgp-part-1-email/ The combination of thunderbird, GPG, and enigmail is the simplest I could come up with. I hope that it helps at least a few of you that might not be well acquainted with encrypting traditional email. Regards, CryptoJunky I just put together a piece on Litecoin following Bitcoin's trends. The full article can be found below: http://cryptojunky.com/blog/2013/11/02/as-bitcoin-climbs-litecoin-follows/ Let me know what you think, does Litecoin have potential as the second largest cryptocurrency, after Bitcoin? - CryptoJunky